Virus
Hydra Virus Explained: What It Is and How to Get Rid of It
Is your PC infected with Hydra Virus? This guide will help you to detect, remove, and prevent this dangerous malware from harming your data.🔍🚨

The hydro virus is a type of Trojan malware. Trojans are harmful programs that disguise themselves as useful software.
However, they secretly perform malicious activities in the background. Note that the Hydra virus often enters the computer through fake downloads, phishing emails, or infected websites.
It can do things like:
- Steal your usernames and passwords.
- Record your keystrokes to track what you type.
- Access your banking information and online transactions.
- Download more malware onto your system.
- Slow down your computer and make it unstable.
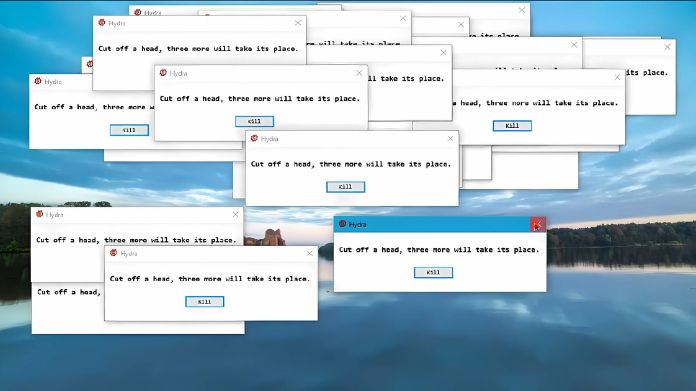
Signs That Your Computer Is Infected
The Hydra virus works in the background. These are the warning signs you should watch out for:
- Your computer slows down suddenly.
- Programs crash or stop responding.
- You see pop-ups and ads even when you’re offline.
- Your browser redirects you to unknown websites.
- Your passwords or online accounts get compromised.
- Your antivirus software stops working.
- You notice strange files or programs you never installed.
If you experience any of these issues, your system may be infected with the Hydra virus.
How Does It Come to Your Device?
Hackers use several tricks to spread the Hydra virus. We have mentioned the most common ways it can infect your computer in the section below.
- Fake Software Downloads: There are many users who download software, games, or files from untrusted sources. Cybercriminals are waiting for this opportunity. They bundle the hydro virus with these downloads. Therefore, when you install the software, the virus secretly enters your system.
- Phishing Emails: Hackers send fake emails and pretend to be from trusted companies like banks, delivery services, or tech support. These emails contain infected attachments or links. The virus installs itself on your computer once you open them.
- Infected websites: All websites are not safe because many of them contain malware. When you visit an infected website, you are exposing your computer or Mobile to Malva. Some websites can secretly install malicious files without your permission. This is called a ”drive-by-download”.
- USB Drives: The Hyderabad virus can transfer to your computer through infected USB drive, external hard drive, or memory card. This method is quite common in the workplace and public computers. Therefore, you must be careful while plugging in external devices.
- Fake Updates: Some websites show fake pop-ups and claim that your system needs an urgent update. You might unknowingly download the Hydra virus if you click on these messages.
The Dangers of Hydra Malware
Hydra is a dangerous banking Trojan that tricks you into granting risky permissions. By default, it requests access to more than 20 different functions on the device.
Now, if you allow these permissions, then the malware gains control over many features. This puts your personal data at risk.
Hydra can infect your device in the following ways.
- Banking credentials: The main goal of Hydra is to steal login details from banking apps. It uses accessibility features to place a fake login screen over the real one. The malware captures the details and sends them to hackers as soon as you enter your username and password.
- OTPs and SMS messages: The virus asks for access to your SMS messages. Many banks use one-time passwords or OTPs for extra security. Hydra can intercept these OTP when it has access to your messages. This allows attacks to bypass multi-factor authentication and access your accounts.
- PINs: Hydra can track your lock screen activity. Additionally, it records the pin you use to unlock your phone. Therefore, hackers can use this information to access your device and authorise unauthorised actions.
- Controls your phone: Some versions of Hydra act as remote access or RAT. This indicates that attackers can control your phone from anywhere. Moreover, they can open apps, steal data, and do harmful actions without you knowing.
- Spams: Hydrogen and mass text messages from your device. Thus, it can send spamming messages to all your contacts. Besides, this spreads the malware to more victims.
- Device settings: Hydra can modify system settings once it gets inside your phone. Besides, it can disable security features like Google Pay Protect. Shockingly, it can turn Wi-Fi and mobile data back on if you switch them off. Hence, Hydra can keep running and stay hidden from detection.
How to Remove Hydra Virus?
You can remove the hydra virus by following the step-by-step guide mentioned below.
1. Disconnect from the Internet

The first thing you should do is disconnect the computer from the Internet. This will prevent the virus from spreading or communicating with its creator.
2. Safe Mode
Now restart the computer and boot it in safe mode. This is a special mode that only loads essential programs which makes it easier to remove the virus.
- Windows: Restart your computer and press F8 (or Shift + F8) before Windows starts loading. Select “Safe Mode” from the menu.
- Mac: Restart your Mac and hold down the Shift key until you see the login screen.
3. Delete Temporary Files
You must delete temporary files as it removes some parts of the virus and frees up space for scanning.
- Windows: Open the Disk Cleanup tool and select “Temporary Files.”
- Mac: Go to Finder, select “Go” from the menu, and choose “Go to Folder.” Type “/private/var/folders” and delete unnecessary files.
4. Run a Virus Scan

You must use a reliable and updated antivirus program to scan your computer.
Some popular antivirus programs include:
- Norton
- McAfee
- Avast
- Malwarebytes
You should run a full system scan and follow the instructions to remove any detected threats.
5. Remove Suspicious Programs

Now, you need to check your list of installed programs and uninstall anything that looks suspicious.
- On Windows, you should head to Control Panel > Programs. Now tap on Uninstall a Program.
- On Mac, you must open Finder and go to Applications. Next, you must drag unwanted programs to the Trash.
Summing Up
The Hydra virus is a serious threat that can steal your personal information and harm your computer.
It spreads through fake downloads, phishing emails, and infected websites. Once inside your system, it can slow down your device, steal passwords, and expose your financial details.
Act quickly if you suspect an infection. You can follow the tips mentioned in the guide to stay safe.