Guides
What is Data Exfiltration? Best Way to Prevent It
Explore the world of data exfiltration and find the best methods to safeguard your data. Discover how to stay one step ahead of cybercriminals.🖥️💀

Do you ever wonder about the security of your data when it leaves your digital fortress? Well, you should be!
Data exfiltration is the cyber world’s silent ninja, stealing sensitive information without your knowledge.
But don’t worry, dear reader, since in our investigation, Hackzon learns the secrets of data exfiltration and the best ways to protect your data from its crafty grasp.
So, take your virtual detective magnifying glass and join us on an adventure to protect your digital assets!
What is Data Exfiltration?
Data exfiltration, commonly referred to as data theft or data exportation, is the unauthorized and frequently covert transportation of data from a computer or device.
This conduct can be performed manually or automatically using malicious software, posing serious cybersecurity risks to individuals, corporations, and government agencies.
Preventing data exfiltration is imperative for several reasons:
- Business Continuity: Data exfiltration can interrupt business, undermine consumer trust, and result in financial losses.
- Regulatory Compliance: Various businesses have severe data privacy and protection rules. Noncompliance might result in harsh sanctions and reputational harm.
- Intellectual Property Protection: Exfiltrated data could compromise trade secrets, research, and other sensitive information essential to an organization’s competitiveness.
Cybercriminals give a high value to sensitive data, utilizing it for illegal reasons such as black market sales, additional intrusions, or ransomware operations.
Detecting and stopping data exfiltration is critical for protecting important data and maintaining data security.
Types of Data Exfiltration Attack Techniques
You’d be shocked at how cunning data exfiltration can be! It has a bundle of tricks and is constantly improving its act to defeat our data security defenses.
Let’s look at some of the regular suspects in data exfiltration and see how they carry off their evil plans.
1. Phishing Attacks
Phishing attacks are a common type of social engineering that uses human psychology to trick people into compromising their security.
Attackers employ email, SMS, or voice communications called vishing to mimic reputable sources.
They aim to fool consumers into downloading malware, providing personal information, or granting access to sensitive data. This deceptive tactic ranges from mass phishing to highly personalized assaults.
Social engineering extends to non-technical approaches like baiting and tailgating, making recognizing and avoiding these deceptive techniques critical.
2. Malware Attacks
Malware assaults frequently attempt data exfiltration via accessing a network’s PCs or mobile devices.
Infected malware harvests data and sends it to an attacker-controlled external server for sale or spread.
These assaults might spread over the network in search of essential company data. Malware may persist and siphon data over time.
3. Outbound Emails
Outbound emails are a typical form of data exfiltration. Employees may utilize personal email or file hosting services for business data, putting themselves in danger.
Attackers use this channel to deliver sensitive data or harmful material.
Email monitoring tools and scanners identify and block outgoing emails carrying sensitive data, protecting various information from exfiltration.
4. Downloads and Uploads
There are two types of data exfiltration: unintentional and malevolent.
In the accidental category, data may be accessed using an unsecured device, jeopardizing its security under corporate security regulations.
On the other hand, malicious insiders purposefully download sensitive information onto trustworthy devices and move it to unprotected ones, placing it in danger of being infiltrated.
It frequently includes cell phones vulnerable to viruses like boot sector or trojans.
These actions highlight the need for strong cybersecurity procedures to prevent data breaches and insider threats.
5. Poor Cloud Hygiene
Poor cloud hygiene refers to the vulnerability of cloud interfaces, which can be abused for data exfiltration by internal or external parties.
Administrators and external attackers may exploit vulnerable cloud storage and virtual machines.
While cloud services have advantages, unsecured use can bring hazards, such as malicious code deployment or unauthorized data access.
How to Detect the Data Exfiltration?
Detecting data exfiltration is critical for protecting sensitive information from external and internal threats.
External assaults sometimes entail the insertion of malware into business network-connected devices, allowing hackers to penetrate, capture, and exfiltrate data invisibly.
On the other hand, insider threats can be malevolent or inadvertent, causing workers to purposefully or unwittingly transfer firm data outside the network.
One detection technique is monitoring network traffic for abnormalities, access patterns, and questionable data flows.
It is critical to thoroughly grasp the organization’s data, categorize it, and encrypt it. Keeping a close eye on all network endpoints, ports, and communication patterns is critical.
Regular risk assessments and vulnerability mitigation are crucial for successful detection and prevention as data exfiltration techniques improve.
How to Prevent Data Exfiltration?
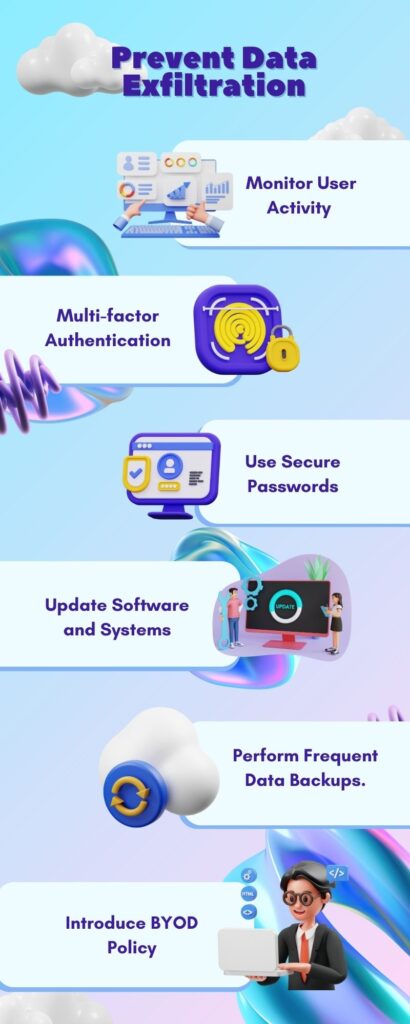
1. Monitor User Activity
To improve security, monitor user activity, trace file access, and detect anomalous behavior to prevent data breaches.
With the advent of remote work, conventional boundaries are eroding, necessitating a greater dependence on software for continuing trust validation and data monitoring.
2. Implement Multi-factor Authentication
Multi-factor authentication improves security by requiring users to give various forms of verification in addition to a username and password.
This strong protocol protects sensitive data and prevents unauthorized access, improving overall system security.
3. Use Secure Passwords
Implement regulations requiring strong passwords of 12+ characters with a combination of capital and lowercase letters, digits, and symbols to improve security.
To protect sensitive information, limit password reuse across different accounts.
4. Regularly Update Software and Systems
Regularly updating software and systems is essential for security. It protects against upcoming risks by patching vulnerabilities in obsolete software, preventing attackers from exploiting them.
5. Perform Frequent Data Backups
Frequent data backups are critical for protecting an organization’s data.
Regular backups ensure the capacity to recover lost or stolen data, acting as a vital safety net in an unanticipated incident or data loss event.
6. Introduce the BYOD (Bring Your Own Device) Policy.
BYOD is a workplace practice that allows employees to utilize personal devices for work-related tasks.
Organizations must develop explicit rules defining device usage restrictions and the appropriate security procedures to reduce the danger of data exfiltration.
Final Thoughts
In an increasingly connected world, protecting your data from exfiltration is essential. We may lower the chance of data exfiltration by being educated about the current threats and applying effective safety techniques.
So, gear up, stay vigilant, and protect your data from prying eyes. Your data’s security is in your hands!🛡️💻