Virus
What is a Logic Bomb? How to Stop It and Prevent Your PC From It
Protect your PC from logic bombs! Learn to identify, stop, and prevent these harmful threats in our expert guide, ensuring your PC’s safety & privacy.

Do you ever worry if your computer contains a ticking time bomb that may destroy your digital life? You might not be that far off! Meet the Logic Bomb, a sneaky danger.
This cunning piece of malicious malware is latent, waiting for the right opportunity to strike and cause havoc on your computer.
Hackzon will dig into the world of logic bombs, deciphering their secret objective and learning how to protect our vital systems from their perilous hold.
Understanding what a logic bomb is and how it works allows us to be alert defenders of our digital castles.
So, let us begin on this information adventure together and discover the mysteries of logic bombs.
We’ll also look into practical techniques to halt them and, even better, keep them from ever compromising our beloved PCs.
Get ready to bolster your cybersecurity arsenal and ensure a safer digital future!
What is a Logic Bomb, in Simple Words?
A logic bomb is a type of malware that is purposefully placed in computer networks, operating systems, or software applications.
It stays inactive until certain circumstances, such as a specified date, time, or system event, are satisfied.
When activated, it can have disastrous results, altering data, destroying files, or even erasing whole hard drives.
Disgruntled insiders seeking vengeance or conducting cyber sabotage deploy logic bombs with other malware like Tumgir, Realsrv, etc, to maximize harm.
Understanding and acting against these hidden risks is critical for preserving digital assets.
How Does a Logic Bomb Work?
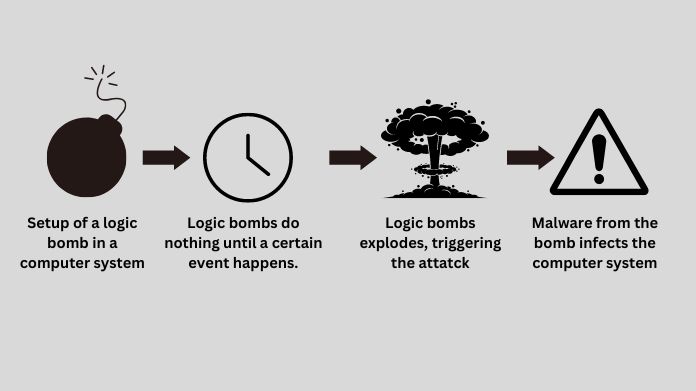
A logic bomb is malicious programming meant to do specified activities based on whether or not certain conditions are satisfied.
These criteria might be positive or negative, indicating that the device will detonate when the condition is met or not met.
When detonated, a logic bomb may inflict considerable harm to a system or organization, with far-reaching consequences.
Understanding how its function is critical for avoiding risks and reducing their impact.
You must take proactive steps to discover and neutralize these harmful bits of code before they cause harm.
What Makes Logic Bombs Dangerous? It’s Characteristics
Logic bombs are deadly because of their secrecy and unexpected payloads. They lay dormant, waiting to strike unexpectedly and catch people by surprise.
Identifying the assailants might be challenging since evidence may be lost during the last phases of the investigation.
This extra time allows criminals to disappear, making them even more dangerous.
Characteristics of Logic Bombs
1. They Are Latent Until They Are Activated
Logic bombs stay dormant until activated. These covert attackers use tiny logic bombs to strike systems from within, avoiding discovery for years.
The payload, or harmful component, dictates the extent of the malware’s impact, ranging from spam dissemination to data theft.
2. They Have an Unidentified Payload.
When malware contains an unknown payload, it becomes inactive. When triggered, the payload performs malicious acts like data theft or spam dissemination across the compromised system.
3. They Deliver the Payload After Meeting Specific Criteria
When specific requirements are satisfied, logic bombs deploy payloads. The detonator, or precondition, conceals them, making detection difficult. Significant events or staff removal set off time bombs within them.
How to Stop Against Logic Bombs Virus and Malware Attacks?
To protect against logic bombs and malware, a multi-layered cybersecurity approach is required, rather than depending exclusively on antivirus software.
Because logic bombs are frequently detonated at a predetermined moment, antivirus software may fail to identify them until too late.
Combining a firewall with antivirus software improves security by preventing possible threats from entering your system.
Backing up corporate data regularly is critical for providing a safety net in the event of a logic bomb assault.
While generating backups takes time, they provide peace of mind by assuring data restoration in the event of an incident.
To protect your computer against it, you must complete efforts to keep your data and systems safe.
How to Prevent Logic Bomb Attacks?

It may be dangerous and inflict extensive damage on your machine. You may, however, defend yourself from these and other malware risks by taking a few easy precautions.
Use the following preventative techniques to safeguard your safety and the security of your devices:
- Use Legit Antivirus Software: Use legitimate antivirus software to safeguard your PC. Reliable anti-malware software prevents infections from occurring by regularly upgrading to combat the most recent threats, guaranteeing a safer online experience.
- Download Nothing Unknown Source: When downloading from unknown sources, use caution. Stick to recognized antivirus software and avoid pirated or shady shareware. To secure your PC, be wary of strange URLs and email attachments.
- Regularly Update OS: Updating your operating system is critical for protecting against malware threats such as logic bombs and ransomware. Developers issue updates regularly, correcting vulnerabilities and guaranteeing the security of your device.
How to Spot a Logic Bomb Attack?
Keep an eye out for unusual computer behavior, particularly when it comes to online activity, to spot a logic bomb.
If you detect anything out of the ordinary, utilize reputable malware removal solutions and, if necessary, seek the advice of a professional.
Knowing your system properly aids in detecting potential attacks and protecting your data.
- Strange Code Alert: Check your computer’s coding frequently to avoid malware. Spot suspicious code to identify future hacks and take immediate action to make your system safer.
- Files Disappear or Change: Be cautious of unusual computer behavior. These assaults can cause mysterious file changes or disappearances, indicating probable data manipulation or malicious intent. Maintain vigilance in the face of such dangers.
- Unauthorized Personal Info Changes: Unauthorised Personal Information Changes may suggest a malware hack. Keep an eye out for changed form data or unexpected password difficulties. For increased protection, be cautious and consider employing event log management solutions.
- Sensitive Data Leaks: Unwanted access to your data, possible hacking, and hidden logic bombs might all jeopardize your cybersecurity.
- Computer Meltdown: It results from logic bombs, widely utilized in ransomware attacks, resulting in various damages such as file lock or data leakage. It might be to blame if your computer performs abnormally for no apparent reason.
- No Reason Restricts Your Access: Have you experienced a denial of access for no apparent reason? A malware assault might prevent you from accessing your computer or shows your IP temporarily blocked. Check for it and notify others if you find one.
Wrapping Words
In today’s digital age, understanding what a logic bomb is and how to safeguard your computer from it is critical. You may prevent such risks by observing your computer’s behavior and researching unexpected indicators.
Using trustworthy malware removal programs and getting expert assistance when necessary offers an extra degree of security.
Stay vigilant!!